As Seen On

Cybersecurity Compliance Checklist: Step-by-Step Framework for Risk Reduction
Download BlueClone's Cybersecurity Compliance Checklist

Why Cybersecurity Compliance Is Critical for Regulated Industries
In today’s highly regulated world, businesses in finance, pharma, insurance, biotechnology, and other sensitive industries can’t afford to fall behind on cybersecurity compliance. The costs of gaps go beyond just risk of fines – they impact your reputation, customer trust, and the day-to-day running of your entire organization. That’s why Blueclone Networks has developed a hands-on, actionable Cybersecurity Compliance Checklist, arming your business with a clear, practical roadmap to bolstering defenses, maintaining regulatory alignment, and staying resilient in the face of ever-evolving cyber risks.

Master Cybersecurity Compliance: Built for Modern, Regulated Businesses
Cybersecurity threats are growing not only in number but in complexity, and regulators are moving fast to keep up. Financial services, healthcare, biotech, insurance, and legal organizations must navigate not one but many overlapping standards – often with significant overlap, ambiguity, and a razor-thin margin for error. Gaps are quickly penalized, with even small infractions drawing scrutiny from auditors and major regulators. This Cybersecurity Compliance Checklist is the missing manual for anyone striving to simplify, or optimize, compliance management as environments and mandates keep shifting.
Download a Proven, Expert-Vetted Compliance Roadmap
If you work in a regulated sector, you already know compliance isn’t just about ticking boxes – it’s about real business resilience. Blueclone Networks’ Cybersecurity Compliance Checklist is designed to go beyond mandated minimums. Our experts have distilled the latest regulatory developments, agency guidance, and real-world client experience into a practical, detailed reference. Whether your concern is HIPAA, SOC 2, NIST, PCI DSS, or multiple frameworks at once, this checklist makes those requirements manageable, so your team can face every review and threat with confidence.
How to Use the Blueclone Cybersecurity Compliance Checklist

Step 1: Download and Distribute
Once you’ve received your free Cybersecurity Compliance Checklist, share it with all members of your IT, compliance, and executive teams. Make sure each department knows which sections are key to their workflows. For example, IT admins can focus on data security checklist items like backup testing, while company leadership should review risk management and regulatory documentation tasks.
Step 2: Conduct an Initial Gap Assessment
Use the checklist to conduct an honest baseline review of your current controls. Mark off everything you already have in place, such as MFA for remote access or incident response playbooks for breach reporting. Anything left unchecked is a clear action item – which you can color-code or assign as a tracked project. Many teams print a working copy or upload it into a project management platform for ongoing review.
Step 3: Prioritize, Assign Ownership, and Set Deadlines
Not every compliance gap carries the same risk, nor does every checklist task require immediate remediation. Categorize your open items by criticality (e.g., “urgent: backups lack offsite redundancy” or “routine: employee cyber awareness training update needed”). Assign a single owner to each task and set internal review deadlines. Teams that use this approach consistently report faster improvements in audit readiness compared to random or fragmented compliance efforts.
Step 4: Attach Evidence and Maintain Audit Trails
For each completed item, attach documentation – like screenshots, system logs, or policies – to your centralized audit folder or governance platform. This habit ensures that, when regulatory inspectors or business partners request proof, you have clear, timestamped evidence. Blueclone’s checklist is designed to integrate with most standard IT documentation systems, making this step seamless for both in-house and co-managed IT departments.
Step 5: Review and Update Regularly
The threat landscape – and regulatory guidance – evolve quickly. Schedule monthly or quarterly reviews of your cybersecurity compliance checklist to ensure controls stay ahead of both business changes and external risks. Add new items as standards change, or as your organization takes on new technology or vendors.
Who Needs This Cybersecurity Compliance Checklist?
Whether you’re managing IT in a fast-growing medical practice, an investment advisory, a biotechnology startup, a legal or insurance firm, or a regional pharmaceutical company, this guide is tailored for you. It’s especially valuable for:
- Compliance officers overseeing risk across multiple frameworks
- IT and security managers juggling daily operations and regulatory milestones
- Executives seeking to strengthen governance and demonstrate due diligence to boards or investors
- In-house and co-managed IT teams who need a unified, actionable tool for compliance collaboration
- Project leaders tasked with audit prep, vendor onboarding, or process improvement in a highly regulated setting
If your organization must protect sensitive data and faces state or federal compliance requirements, this checklist is essential.

Why Download This Cybersecurity Compliance Checklist?
Regulations like HIPAA, FINRA, PCI DSS, NIST, and SOC 2 set a demanding bar for information security. Too often, firms miss important steps, misinterpret requirements, or fail to catch where their controls are thin. For business and IT leaders, missing the mark risks everything from punitive fines to loss of customer confidence, not to mention business disruption if something goes wrong.
That’s where this step-by-step, expert-vetted Cybersecurity Compliance Checklist delivers serious value for your entire team. Here’s how your business will benefit:
1. Practical and Comprehensive Coverage
- Data Protection: Clear steps for data encryption, backups, and retention/purge policies, avoiding costly breaches or loss of sensitive data.
- Access Control: Know exactly how to safeguard user access with MFA, privilege rules, and regular audits – protecting your business from inside and out.
- Incident Response: Detailed, field-ready plans to ensure rapid containment and clear reporting when incidents occur, reducing downtime and post-breach costs.
- Risk Management: Ongoing processes for risk assessment, vendor oversight, and vulnerability response.
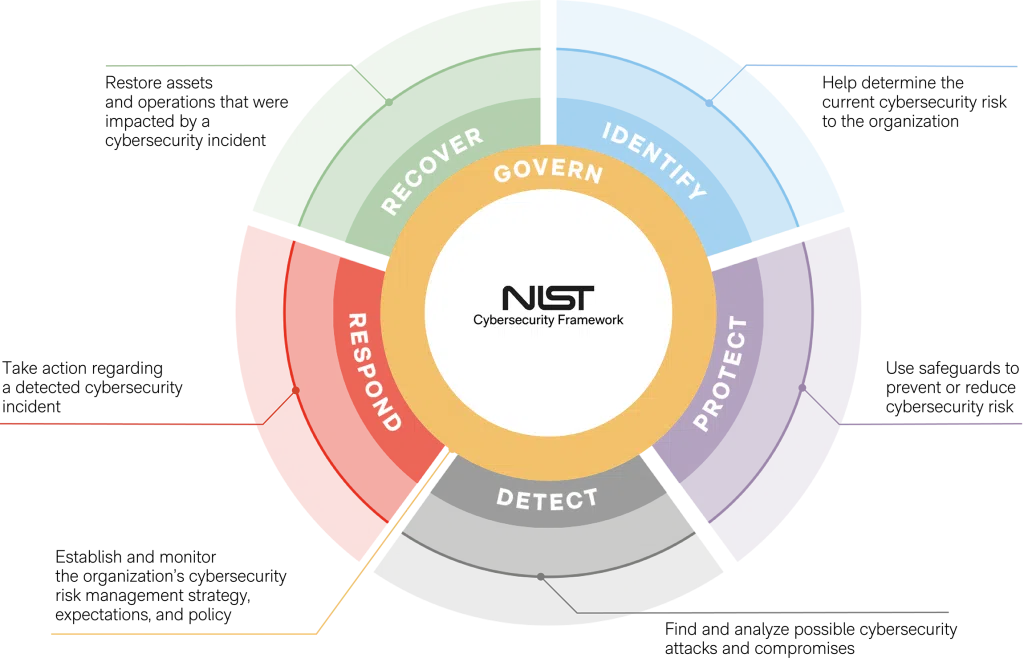
- Regulatory Alignment: Easy mapping to major frameworks – HIPAA, FINRA, NIST, PCI DSS – ensuring you can demonstrate readiness during any audit.
2. Quick-Reference, Actionable Format
No fluff – just the tasks and checks security and compliance teams genuinely rely on. The checklist includes:
- Direct action items
- Room for your own notes and tracking progress
- Alignment with the latest 2024 guidance from major industry frameworks and agencies
3. Designed for Regulated Industries
Built with input from Blueclone’s seasoned compliance experts, the checklist tackles real issues facing legal, healthcare, finance, and life sciences firms – including third-party risks, reporting requirements, and pressing cyber threats (from phishing to ransomware).
4. Saves Time, Cuts Confusion
Whether you’re preparing for your next audit, retraining your team, or responding to new regulations – this checklist keeps your process clear and focused, no matter how complex your business or IT environment may be.
Why Most Compliance Efforts Fall Short (and How the Right Checklist Bridges the Gap)
Many business leaders assume their controls are in good shape until they face a real-world breach, auditor, or legal discovery process. The reality? According to recent studies, over 65% of SMBs in regulated industries fall short on at least one major requirement in a standard regulatory framework like NIST, HIPAA, or PCI DSS – even when they already have compliance processes in place.
Common reasons compliance efforts miss the mark include:
- Relying on out-of-date templates that don’t reflect evolving regulations
- Not mapping controls to all relevant standards (missing cross-requirements)
- Failing to document changes, exceptions, or responsibilities
- Overlooking vendor and third-party risks
- Relying on verbal processes instead of written evidence
This guide was created by Blueclone Networks to challenge those pitfalls – laying out an end-to-end reference you’ll return to with every policy review, onboarding, tabletop exercise, and audit.

Understanding the High Stakes: Regulatory Compliance in Sensitive Industries
With regulations tightening across finance, healthcare, pharma, and legal sectors, the stakes for non-compliance have never been higher. Data breaches in the finance sector, for example, can trigger both crippling regulatory fines and massive reputational losses. The average healthcare breach now exceeds $10 million in cost, often compounding with class-action liability. Legal and insurance firms face growing scrutiny for client confidentiality lapses and third-party vendor risk. In each of these industries, regulatory compliance is an executive priority – not just an IT checkbox.
Examples of Real-World Compliance Failures
- A regional pharmacy chain suffered a $1.1 million fine after an outdated retention policy led to thousands of unencrypted records being exposed during a ransomware attack.
- A financial advisor network failed a FINRA audit when user access logs were incomplete and incident response documentation was missing – resulting in six months of costly remediation work.
- One law firm lost a seven-figure insurance policy payout after a breach, due to a missing written incident response plan and outdated access control reviews.
These examples underline why investing in a holistic cybersecurity compliance checklist isn’t just wise – it’s essential for survival and success.
What’s Inside: Key Elements of Our Cybersecurity Compliance Checklist
Data Protection
- Encrypt sensitive customer and firm data throughout the organization
- Maintain offsite, redundant backups – don’t let hardware failures or ransomware result in catastrophic data loss
- Run periodic tests of backups and establish tailored data retention and disposal policies
Access Control
- Require multi-factor authentication (MFA) for every user, from executives to interns
- Limit access privileges by business need; review, update, and prune user rights regularly
- Document and audit access reviews as part of your compliance workflow
Incident Response
- Maintain a clear, up-to-date incident response plan – tested through tabletop exercises
- Appoint a breach response team with designated roles and responsibilities
- Include collection requirements for logs, forensic evidence, and regulatory reporting
Risk Management
- Conduct thorough risk assessments each year, with prioritized remediation
- Map vendor relationships – ensure partners and suppliers meet your compliance standards
- Keep a living log of vulnerabilities and remediation milestones
Regulatory Alignment
- Align your controls with key frameworks like HIPAA, NIST, FINRA, PCI DSS – using intuitive tables for tracking gap closure
- Centralize audit records and update documentation with any policy or system change
- Monitor regulatory updates and adjust protocols to keep your controls future-proof
How the Cybersecurity Compliance Checklist Fits Into Your Broader Compliance Strategy
Security checklists aren’t just for annual audits or regulatory snapshots – they’re the cornerstone of an ongoing compliance strategy. Our Cybersecurity Compliance Checklist fits seamlessly into your organization’s continuous improvement process. By breaking down requirements into manageable actions and frequent check-ins, you create a living compliance culture. This proactive approach helps detect gaps early, ensures consistent controls, and provides evidence of diligence should regulators or partners request proof of your compliance readiness.
Supporting Your Team – From IT Managers to C-Level Executives
Whether you’re a CIO orchestrating IT policy, a compliance officer reviewing audit evidence, or a business owner accountable for cybersecurity and privacy, this checklist guides informed decisions at every level. IT managers use it to prioritize projects, assign responsibility, and demonstrate completion. Executives rely on it for board reporting and risk communication, knowing that every item aligns to actual regulatory controls – not just best guesses.
Empower In-House and Co-Managed IT Departments
Blueclone Networks serves both businesses with internal IT staff seeking co-managed solutions and those relying on fully managed services. The checklist’s structure offers clarity and delegation – making it easy to divide responsibility between internal teams and Blueclone’s experts. This collaborative approach fosters accountability and smooth communication during compliance initiatives, especially when scaling or onboarding new staff or vendors.
Ready to Move Beyond the Minimum? Secure Your Business and Prove Compliance
No matter how big or small your business, cybersecurity compliance is more than ticking boxes – it’s a year-round commitment that requires precision, vigilance, and the right tools. Start building a stronger cybersecurity posture with the same practical checklist Blueclone’s risk and compliance consultants use every day to help businesses like yours pass audits, block threats, and focus on growth.
Don’t leave compliance to chance. Download the Free Cybersecurity Compliance Checklist and take control of your IT readiness.
The Importance of a Cybersecurity Compliance Checklist for Different Sectors
Each regulated industry faces a unique compliance environment. Healthcare organizations wrestle with HIPAA and HITECH obligations, often needing to demonstrate end-to-end information security management, while financial services must contend with the demands of FINRA, SEC, and PCI DSS on top of evolving privacy requirements. Legal professionals have ethical and regulatory duties to safeguard client data, and biotech or pharmaceutical businesses increasingly encounter both FDA guidance and intricate data residency mandates. Failing to align policies, procedures, and technical controls across multiple compliance frameworks invites audit headaches and missed business opportunities.
For example, a healthcare provider conducting telemedicine must map both HIPAA privacy rules and payment card standards if processing co-pays online. Similarly, insurance agencies managing medical records might be subject to both state insurance department audits and federal IT security requirements. The Blueclone Cybersecurity Compliance Checklist unifies these moving target requirements – breaking complex mandates into actionable best practices such as data encryption checklists, vendor due diligence templates, and incident response compliance checklists.
Why Checklists Drive Better Cybersecurity Outcomes
Research published by Harvard University and leading compliance organizations shows that well-designed checklists can reduce human error by up to 40% in complex operational environments – including cybersecurity. In the context of a fast-changing threat landscape and evolving regulations, this means:
- Improved consistency: Each audit or control review follows the same, systematic process – minimizing the risk of overlooked checklist items.
- Accountability: Clearly documented action items support internal audits, external reviews, and due diligence exercises.
- Quicker remediation: With a prioritized IT compliance checklist, your team can see at-a-glance where gaps exist, ensuring faster action and documenting improvements for stakeholders.
A cybersecurity best practices checklist is not just a compliance tool – it’s a practical roadmap for securing sensitive operations. By combining regulatory compliance checklists (NIST compliance checklist, PCI DSS compliance checklist, and others) in one reference, Blueclone gives your organization the structure and peace of mind needed to operate securely.
Should You Partner With Blueclone Networks?
If you’re asking yourself if Blueclone Networks is the right NJ-based IT solution for your business, consider these benefits
Maximum Uptime
Ensure your systems are always operational with minimal downtime.
Friendly and Prompt Communication
Approachable and responsive support for all your IT queries.
A US-Based SOC
Benefit from a Security Operations Center based in the United States.
Proven Reputation
Trust in our track record of delivering exceptional IT solutions.
Proactive Compliance
Stay compliant with the latest standards and practices.
Customized Plans for Each Client
Tailored IT strategies to meet your specific business needs.
Years of Relevant Experience
Leverage our extensive expertise for your IT success.

Serving Key Locations in New Jersey
We proudly serve various locations across New Jersey, including:
- Princeton, NJ: Offering specialized network support services to businesses in the Princeton area. Princeton is a hub for innovation, home to major institutions and tech startups.
- Lawrenceville, NJ: Providing comprehensive managed IT services tailored to the needs of Lawrenceville businesses.
- Hamilton, NJ: Delivering reliable managed IT services to support the growth and efficiency of Hamilton-based companies. Hamilton is one of the largest townships in NJ, known for its diverse business community.
Frequently Asked Questions (FAQ)
The checklist is designed to map directly to regulatory requirements like HIPAA, NIST, FINRA, and PCI DSS. By following each task, you’ll conduct a broad self-assessment, document your steps, and address areas most commonly found lacking during official audits. This structured approach saves time, minimizes risk, and keeps your business audit-ready all year.
Yes. This version reflects current requirements and best practices as of 2025, incorporating updates from FINRA, NIST, and other relevant bodies. Blueclone’s consultants monitor ongoing regulatory changes and adapt the checklist regularly to help you stay ahead of new compliance mandates.
Absolutely. Blueclone Networks is committed to data privacy and security. All form submissions are encrypted, handled according to the strictest policies, and will never be sold or shared. The company provides IT solutions for regulated industries and applies the same standards to client contacts as to its own sensitive data.
Yes. The checklist is modular, with references for HIPAA, SOC 2, PCI DSS, NIST, and finance-specific regulations. If your business is subject to multiple requirements, the document helps you track overlapping obligations and map controls accordingly.
With nearly two decades supporting regulated firms, Blueclone brings regional expertise and national recognition to small and mid-sized organizations. The firm pairs technical know-how with a transparent, client-first approach – delivering compliance services, IT support, and real-world advice local leaders trust. From audits and risk assessments to training and incident response, Blueclone equips you with tools and guidance to pass stringent reviews and block the latest cyber threats.
About Blueclone Networks
Established in 2006, Blueclone Networks has been a trusted provider of IT solutions in New Jersey. Our commitment to excellence and customer satisfaction has positioned us as a leading network support company in NJ. We pride ourselves on delivering services that not only meet but exceed our clients’ expectations.